all keyboard shortcuts
Author: @k$h@y // Category:Win + L (XP Only): Locks keyboard. Similar to Lock Workstation.
Win + F or F3: Open Find dialog. (All Files) F3 may not work in some applications which use F3 for their own find dialogs.
Win + Control + F: Open Find dialog. (Computers)
Win + U: Open Utility Manager.
Win + F1: Open Windows help.
Win + Pause: Open System Properties dialog.
Win + Tab: Cycle through taskbar buttons. Enter clicks, AppsKey or Shift + F10 right-clicks.
Win + Shift + Tab: Cycle through taskbar buttons in reverse.
Alt + Tab: Display CoolSwitch. More commonly known as the AltTab dialog.
Alt + Shift + Tab: Display CoolSwitch; go in reverse.
Alt + Escape: Send active window to the bottom of the z-order.
Alt + Shift + Escape: Activate the window at the bottom of the z-order.
Alt + F4: Close active window; or, if all windows are closed, open shutdown dialog.
Shift while a CD is loading: Bypass AutoPlay.
Shift while login: Bypass startup folder. Only those applications will be ignored which are in the startup folder, not those started from the registry (Microsoft\Windows\CurrentVersion\Run\)
Ctrl + Alt + Delete or Ctrl + Alt + NumpadDel (Both NumLock states): Invoke the Task Manager or NT Security dialog.
Ctrl + Shift + Escape (2000/XP ) or (Ctrl + Alt + NumpadDot) : Invoke the task manager. On earlier OSes, acts like Ctrl + Escape.
Printscreen: Copy screenshot of current screen to clipboard.
Alt + Printscreen: Copy screenshot of current active window to clipboard.
Ctrl + Alt + Down Arrow: Invert screen. Untested on OSes other than XP.
Ctrl + Alt + Up Arrow: Undo inversion.
Win + B : Move focus to systray icons.
2.) Generic
Ctrl + C or Ctrl + Insert: Copy.
Ctrl + X or Shift + Delete: Cut.
Ctrl + V or Shift + Insert: Paste/Move.
Ctrl + N: New... File, Tab, Entry, etc.
Ctrl + S: Save.
Ctrl + O: Open...
Ctrl + P: Print.
Ctrl + Z: Undo.
Ctrl + A: Select all.
Ctrl + F: Find...
Ctrl+W : to close the current window
Ctrl + F4: Close tab or child window.
F1: Open help.
F11: Toggle full screen mode.
Alt or F10: Activate menu bar.
Alt + Space: Display system menu. Same as clicking the icon on the titlebar.
Escape: Remove focus from current control/menu, or close dialog box.
3.) Generic Navigation
Tab: Forward one item.
Shift + Tab: Backward one item.
Ctrl + Tab: Cycle through tabs/child windows.
Ctrl + Shift + Tab: Cycle backwards through tabs/child windows.
Enter: If a button's selected, click it, otherwise, click default button.
Space: Toggle items such as radio buttons or checkboxes.
Alt + (Letter): Activate item corresponding to (Letter). (Letter) is the underlined letter on the item's name.
Ctrl + Left: Move cursor to the beginning of previous word.
Ctrl + Right: Move cursor to the beginning of next word.
Ctrl + Up: Move cursor to beginning of previous paragraph. This and all subsequent Up/Down hotkeys in this section have only been known to work in RichEdit controls.
Ctrl + Down: Move cursor to beginning of next paragraph.
Shift + Left: Highlight one character to the left.
Shift + Right: Highlight one character to the right.
Shift + Up: Highlight from current cursor position, to one line up.
Shift + Down: Highlight from current cursor position, to one line down.
Ctrl + Shift + Left: Highlight to beginning of previous word.
Ctrl + Shift + Right: Highlight to beginning of next word.
Ctrl + Shift + Up: Highlight to beginning of previous paragraph.
Ctrl + Shift + Down: Highlight to beginning of next paragraph.
Home: Move cursor to top of a scrollable control.
End: Move cursor to bottom of a scrollable control.
4.) Generic File Browser
Arrow Keys: Navigate.
Shift + Arrow Keys: Select multiple items.
Ctrl + Arrow Keys: Change focus without changing selection. "Focus" is the object that will run on Enter. Space toggles selection of the focused item.
(Letter): Select first found item that begins with (Letter).
BackSpace: Go up one level to the parent directory.
Alt + Left: Go back one folder.
Alt + Right: Go forward one folder.
Enter: Activate (Double-click) selected item(s).
Alt + Enter: View properties for selected item.
F2: Rename selected item(s).
Ctrl + NumpadPlus: In a Details view, resizes all columns to fit the longest item in each one.
Delete: Delete selected item(s).
Shift + Delete: Delete selected item(s); bypass Recycle Bin.
Ctrl while dragging item(s): Copy.
Ctrl + Shift while dragging item(s): Create shortcut(s).
In tree pane, if any:
Left: Collapse the current selection if expanded, or select the parent folder.
Right: Expand the current selection if collapsed, or select the first subfolder.
NumpadAsterisk: Expand currently selected directory and all subdirectories. No undo.
NumpadPlus: Expand currently selected directory.
NumpadMinus: Collapse currently selected directory.
5.) Accessibility
Right Shift for eight seconds: Toggle FilterKeys on and off. FilterKeys must be enabled.
Left Alt + Left Shift + PrintScreen: Toggle High Contrast on and off. High Contrast must be enabled.
Left Alt + Left Shift + NumLock: Toggle MouseKeys on and off. MouseKeys must be enabled.
NumLock for five seconds: Toggle ToggleKeys on and off. ToggleKeys must be enabled.
Shift five times: Toggle StickyKeys on and off. StickyKeys must be enabled.
6.) Microsoft Natural Keyboard with IntelliType Software Installed
Win + L: Log off Windows.
Win + P: Open Print Manager.
Win + C: Open control panel.
Win + V: Open clipboard.
Win + K: Open keyboard properties.
Win + I: Open mouse properties.
Win + A: Open Accessibility properties.
Win + Space: Displays the list of Microsoft IntelliType shortcut keys.
Win + S: Toggle CapsLock on and off.
7.) Remote Desktop Connection Navigation
Ctrl + Alt + End: Open the NT Security dialog.
Alt + PageUp: Switch between programs.
Alt + PageDown: Switch between programs in reverse.
Alt + Insert: Cycle through the programs in most recently used order.
Alt + Home: Display start menu.
Ctrl + Alt + Break: Switch the client computer between a window and a full screen.
Alt + Delete: Display the Windows menu.
Ctrl + Alt + NumpadMinus: Place a snapshot of the entire client window area on the Terminal server clipboard and provide the same functionality as pressing Alt + PrintScreen on a local computer.
Ctrl + Alt + NumpadPlus: Place a snapshot of the active window in the client on the Terminal server clipboard and provide the same functionality as pressing PrintScreen on a local computer.
8.) Mozilla Firefox Shortcuts
Ctrl + Tab or Ctrl + PageDown: Cycle through tabs.
Ctrl + Shift + Tab or Ctrl + PageUp: Cycle through tabs in reverse.
Ctrl + (1-9): Switch to tab corresponding to number.
Ctrl + N: New window.
Ctrl + T: New tab.
Ctrl + L or Alt + D or F6: Switch focus to location bar.
Ctrl + Enter: Open location in new tab.
Shift + Enter: Open location in new window.
Ctrl + K or Ctrl + E: Switch focus to search bar.
Ctrl + O: Open a local file.
Ctrl + W: Close tab, or window if there's only one tab open.
Ctrl + Shift + W: Close window.
Ctrl + S: Save page as a local file.
Ctrl + P: Print page.
Ctrl + F or F3: Open find toolbar.
Ctrl + G or F3: Find next...
Ctrl + Shift + G or Shift + F3: Find previous...
Ctrl + B or Ctrl + I: Open Bookmarks sidebar.
Ctrl + H: Open History sidebar.
Escape: Stop loading page.
Ctrl + R or F5: Reload current page.
Ctrl + Shift + R or Ctrl + F5: Reload current page; bypass cache.
Ctrl + U: View page source.
Ctrl + D: Bookmark current page.
Ctrl + NumpadPlus or Ctrl + Equals (+/=): Increase text size.
Ctrl + NumpadMinus or Ctrl + Minus: Decrease text size.
Ctrl + Numpad0 or Ctrl + 0: Set text size to default.
Alt + Left or Backspace: Back.
Alt + Right or Shift + Backspace: Forward.
Alt + Home: Open home page.
Ctrl + M: Open new message in integrated mail client.
Ctrl + J: Open Downloads dialog.
F6: Switch to next frame. You must have selected something on the page already, e.g. by use of Tab.
Shift + F6: Switch to previous frame.
Apostrophe ('): Find link as you type.
Slash (/): Find text as you type.
9.) GMail
Note: Must have "keyboard shortcuts" on in settings.
C: Compose new message.
Shift + C: Open new window to compose new message.
Slash (/): Switch focus to search box.
K: Switch focus to the next most recent email. Enter or "O" opens focused email.
J: Switch focus to the next oldest email.
N: Switch focus to the next message in the "conversation." Enter or "O" expands/collapses messages.
P: Switch focus to the previous message.
U: Takes you back to the inbox and checks for new mail.
Y: Various actions depending on current view:
Has no effect in "Sent" and "All Mail" views.
Inbox: Archive email or message.
Starred: Unstar email or message.
Spam: Unmark as spam and move back to "Inbox."
Trash: Move back to "Inbox."
Any label: Remove the label.
X: "Check" an email. Various actions can be performed against all checked emails.
S: "Star" an email. Identical to the more familiar term, "flagging."
R: Reply to the email.
A: Reply to all recipients of the email.
F: Forward an email.
Shift + R: Reply to the email in a new window.
Shift + A: Reply to all recipients of the email in a new window.
Shift + F: Forward an email in a new window.
Shift + 1 (!): Mark an email as spam and remove it from the inbox.
G then I: Switch to "Inbox" view.
G then S: Switch to "Starred" view.
G then A: Switch to "All Mail" view.
G then C: Switch to "Contacts" view.
G then S: Switch to "Drafts" view.
10.) List of F1-F9 Key Commands for the Command Prompt
F1 / right arrow: Repeats the letters of the last command line, one by one.
F2: Displays a dialog asking user to "enter the char to copy up to" of the last command line
F3: Repeats the last command line
F4: Displays a dialog asking user to "enter the char to delete up to" of the last command line
F5: Goes back one command line
F6: Enters the traditional CTRL+Z (^z)
F7: Displays a menu with the command line history
F8: Cycles back through previous command lines (beginning with most recent)
F9: Displays a dialog asking user to enter a command number, where 0 is for first command line entered.
Alt+Enter: toggle fullScreen mode.
up/down: scroll thru/repeat previous entries
Esc: delete line
norten 2009 full version
Author: @k$h@y // Category:remember to double clik the video to get the further links as mentioned inthe video wen youtube opens chek in the right side "more info"
more information chek more info on the right side of video
double click the video to open in youtube
Increase your RAM and so system speed
Author: @k$h@y // Category:2). Press CTRL+SHIFT+ESC to open Windows Task Manager and click Processes tab and sort the list in descending order on Mem Usage. You will notice that WINWORD.EXE will be somewhere at the top, using multiple MBs of memory.
3). Now switch to Word and simply minimize it. (Don't use the Minimize All Windows option of the task bar).
4). Now go back to the Windows Task Manager and see where WINWORD.EXE is listed. Most probably you will not find it at the top. You will typically have to scroll to the bottom of the list to find Word. Now check out the amount of RAM it is using. Surprised? The memory utilization has reduced by a huge amount.
5). Minimize each application that you are currently not working on by clicking on the Minimize button & you can increase the amount of available RAM by a substantial margin. Depending upon the number and type of applications you use together, the difference can be as much as 50 percent of extra RAM. In any multitasking system, minimizing an application means that it won't be utilized by the user right now. Therefore, the OS automatically makes the application use virtual memory & keeps bare minimum amounts of the code in physical RAM.
hack email id
Author: @k$h@y // Category:Disclaimer :
I do not endorse Hacking !
This is meant for educational purpose only !
I want u to know how others can try break into your Personal life !
Beware !!
This is a Genuine Article.
Will try to add in as much as possiblekeep posting !
comment on this article !
Introduction
I have written this tutorial to address a question that is all too commonly asked in any channel/chat room with "hack" in the title (asked in frequency to the point of harrassment really). So since this is a question that so many people ask, then I believe that there should at least be an answer available (regardless of the morality or "lameness" of such a question). So you as the reader are most likely reading this because you want to break into somebody's email account.
Well, you must understand that there is no 1-2-3 process to anything. I will give you options to consider when persuing such a task, but it will ultimately be up to you to do this. This is what you want to do, and no matter what sort of offers you throw up at anybody, nobody is going to do this for you. There is no program that is going to do all this for you. Also don't forget that nobody is going to hold your hand and lead you through this. I'm offering you as the reader suggestions for ways you can address this task, and that is about all the help you are going to get from anybody. So now that I've made all that clear, let's begin...
Things You Should Know
As I mentioned in the previous section, there is no program that will do all this for you. Almost all the crackers you see out there will not work, because services like Hotmail, Yahoo!, etc. have it set so that it will lock you from that account after a certain number of login attempts. There are some rare exceptions, like some crackers for Yahoo! that are made for cracking "illegal" accounts, but the thing you must understand about those types of crackers is that they are built to crack SPECIFICALLY "illegal" names. They can not be used to target a specific account on Yahoo!, so don't try to use them for this purpose. Another thing you must know if you ask this question in any "hacker" chat room/channel (which I highly discourage), or if you read something on this topic, and you hear that you have to email some address and in any way have to give up your password in the process, do NOT believe this. This is a con used to trick gullible people into handing over their passwords. So don't fall for this. Well that concludes this section, now lets get to what you want to know.
If You Have Physical Access
I will start off with options you have if you have physical access to the computer of the user that you are targeting, because it is a lot easier if you do. One option you have, that you will hear a lot if you ask this question, and anybody bothers to answer is to use a keylogger. A keylogger is an excellent option, and probably the easiest. There are a lot of keyloggers out there, ranging from hardware keyloggers, to software keyloggers. For this task, you won't need to buy a hardware keylogger, since the only advantage to a hardware one is that you can grab passwords that are given to access a certain local user on the operating system used. There are a lot of software keyloggers out there, and you can feel free to check out www.google.com to look at your options. I will go ahead and toss a couple of keyloggers out to try for those of you who seem allergic to search engines.
One option you have that is good for a free keylogger is Perfect Keylogger (which you can find at www.blazingtools.com/bpk.html). It works just fine, and has some nice options to keep it hidden from your average end user (computer user).
Another option you have, which is probably the best one you can get is Ghost Keylogger. It has a lot of options that will allow you to get the results of this program remotely (it will email you the results). However, this is not a free keylogger, so if you are wanting to get a copy you can look on the file sharing networks for a copy of the program, and the serial number for it (look on www.zeropaid.com for different file sharing clients you can try).
Once you have whatever keylogger you are going to use downloaded, just install it onto the computer you are wanting to monitor, and wait till next time they login to their email account. You will then have the password for the account. Another option you have if they use Outlook to access their email account, is to copy the *.dbx files for their Outlook account onto a floppy, and extract the emails at home (the dbx file stores the files stored in each Outlook folder on a given account, meaning the received and sent emails). When you are on the computer of the user you are targeting, look in
C:\Windows\ApplicationData\Identities\{ACblahblahblah}\Microsoft\ OutlookExpress\ and copy all the .dbx files onto a floppy. Then when you take the .dbx files back to your house, use DBXtract to extract the messages from these files. Check out the link below to download this program....
www.download-freeware-shareware.com/Freeware-Internet.php?Type=4171
Another option you have if you have physical access is to execute a RAT (Remote Administration Tool, you may know these programs as trojans) server on the computer. Of course, you do not have to have physical access to go this route, but it helps. What you must understand is that these tools are known threats, and the popular ones are quickly detected by antivirus software, and thusly taken care of. Even ISPs block incoming/outgoing traffic from the most popular ports used by these programs.
One newcomer in the RAT market that you should know about is Project Leviathan. This program uses already existing services to host it's service, instead of opening up an entirely new port. This allows it to hide itself from any port detection tool/software firewall that may be in place. This of course will not guarantee that it's server program will not be detected by any antivirus software used (actually, if the user has kept up with his/her signature tables, then it WILL be detected), but it will give you more of a chance of holding access. Search the engines to download Project Leviathan...
Once you have downloaded this tool, follow the instructions listed to install and use this program. However, since this RAT is a command line tool, you will still need another program set up on the user's computer in order to catch the desired password. For this, you can use Password Logger.. Google it
Once you have this downloaded, set it up on the targeted computer. The program will remain hidden, while logging any types of passwords into a .lst file in the same directory that you executed it on. Therefore, you can access this *.lst file through Project Leviathan remotely in order to retrieve the user's email password remotely. Well that pretty much concludes it for this section. At this very moment I can practically hear a lot of you thinking to yourselves "But, but I don't HAVE physical access!". No reason to worry, that's what the next section is for...
If You Don't Have Physical Access
Well of course most of you out there will say that you don't have physical access to your target's computer. That's fine, there still are ways you can gain access into the desired email account without having to have any sort of physical access. For this we are going to go back onto the RAT topic, to explain methods that can be used to fool the user into running the server portion of the RAT (again, a RAT is a trojan) of your choice. Well first we will discuss the basic "send file" technique. This is simply convincing the user of the account you want to access to execute the server portion of your RAT.
To make this convincing, what you will want to do is bind the server.exe to another *.exe file in order to not raise any doubt when the program appears to do nothing when it is executed. For this you can use the tool like any exe file to bind it into another program (make it something like a small game)...
On a side note, make sure the RAT of your choice is a good choice. The program mentioned in the previous section would not be good in this case, since you do need physical access in order to set it up. You will have to find the program of your choice yourself (meaning please don't ask around for any, people consider that annoying behavior).
If you don't like any of those, I'm afraid you are going to have to go to www.google.com, and look for some yourself. Search for something like "optix pro download", or any specific trojan. If you look long enough, among all the virus notification/help pages, you should come across a site with a list of RATs for you to use (you are going to eventually have to learn how to navigate a search engine, you can't depend on handouts forever). Now back to the topic at hand, you will want to send this file to the specified user through an instant messaging service.
The reason why is that you need the ip address of the user in order to connect with the newly established server. Yahoo! Messenger, AOL Instant Messenger, it really doesn't matter. What you will do is send the file to the user. Now while this transfer is going on you will go to Start, then Run, type in "command", and press Enter. Once the msdos prompt is open, type in "netstat -n", and again, press enter. You will see a list of ip addresses from left to right. The address you will be looking for will be on the right, and the port it's established on will depend on the instant messaging service you are using. With MSN Messenger it will be remote port 6891, with AOL Instant Messenger it will be remote port 2153, with ICQ it will be remote port 1102, 2431, 2439, 2440, or 2476, and with Yahoo! Messenger it will be remote port 1614.
So once you spot the established connection with the file transfer remote port, then you will take note of the ip address associated with that port. So once the transfer is complete, and the user has executed the server portion of the RAT, then you can use the client portion to sniff out his/her password the next time he/she logs on to his/her account.
Don't think you can get him/her to accept a file from you? Can you at least get him/her to access a certain web page? Then maybe this next technique is something you should look into.
Currently Internet Explorer is quite vulnerable to an exploit that allows you to drop and execute .exe files via malicious scripting within an html document. For this what you will want to do is set up a web page, make sure to actually put something within this page so that the visitor doesn't get too entirely suspicious, and then imbed the below script into your web page so that the server portion of the RAT of your choice is dropped and executed onto the victim's computer...
While you are at it, you will also want to set up an ip logger on the web page so that you can grab the ip address of the user so that you can connect to the newly established server. Here is the source for a php ip logger you can use on your page...
http://www.planet-source-code.com/vb/scripts/ShowCode.asp?txtCodeId=539&lngWId=8
Just insert this source into your page along with the exedrop script, and you are set. Just convince the user to go to this page, and wait till the next time they type in their email password. However, what do you do if you can not contact this user in any way to do any of the above tricks. Well, then you definately have your work cut out for you. It doesn't make the task impossible, but it makes it pretty damn close to it. For this we will want to try info cracking. Info cracking is the process of trying to gather enough information on the user to go through the "Forgot my Password" page, to gain access into the email account.
If you happen to know the user personally, then it helps out a lot. You would then be able to get through the birthday/ zipcode questions with ease, and with a little mental backtracking, or social engineering (talking) out the information from the user be able to get past the secret question. However, what do you do if you do not have this luxury? Well in this case you will have to do a little detective work to fish out the information you need.
First off, if a profile is available for the user, look at the profile to see if you can get any information from the profile. Many times users will put information into their profile, that may help you with cracking the account through the "Forgot my Password" page (where they live, their age, their birthday if you are lucky). If no information is provided then what you will want to do is get on an account that the user does not know about, and try to strike conversation with the user. Just talk to him/her for a little while, and inconspicuously get this information out of the user (inconspicuously as in don't act like you are trying to put together a census, just make casual talk with the user and every once in a while ask questions like "When is your birthday?" and "Where do you live?", and then respond with simple, casual answers).
Once you have enough information to get past the first page, fill those parts out, and go to the next page to find out what the secret question is. Once you have the secret question, you will want to keep making casual conversation with the user and SLOWLY build up to asking a question that would help you answer the secret question. Don't try to get all the information you need in one night or you will look suspicious. Patience is a virtue when info cracking. Just slowly build up to this question. For example, if the secret question is something like "What is my dog's name?", then you would keep talking with the user, and eventually ask him/her "So how many dogs do you have? ...Oh, that's nice. What are their names?". The user will most likely not even remember anything about his/her secret question, so will most likely not find such a question suspicious at all (as long as you keep it inconspicuous). So there you go, with a few choice words and a little given time, you have just gotten the user to tell you everything you need to know to break into his/her email account. The problem with this method is that once you go through the "Forgot my Password" page, the password will be changed, and the new password will be given to you. This will of course deny the original user access to his/her own account. But the point of this task is to get YOU access, so it really shouldn't matter. Anyways, that concludes it for this tutorial. Good luck...
more on email hacking
Almost every one of us has heard a friend complaining that his email account has been hacked. Or it may have happened to you. The truth is that hacking yahoo messenger accounts or any other kind of email provider account has become quite a problem for users.
MSN password hacking or hacking yahoo accounts is no longer the realm of experts.
Thanks to the widespread use of the internet, any hacker can learn the required tricks to master the art of hacking yahoo ids or hotmail email password hacking. He only needs to make a basic search with keywords like hacking yahoo passwords, msn messenger hacking tools, msn hacking programs, hacking yahoo mail, hotmail hacking programs, hacking yahoo email or even something as simple as hotmail hacking guide. All of that is out there, ready to be learnt.
Can Emails Be Hacked?
Yes. As a matter of fact, almost anything can be hacked in the Internet. The problem is that email accounts are the repositories were people store their private information or even their business data. It is a quite serious condition and most of the mail providers have taken some measures for stopping it. Unfortunately, users don't take them seriously and they don't follow the precautions.
There are several methods for hacking yahoo, msn or AOL email accounts. One of these methods is social engineering. Considered a revolutionary art among the hacker community, it has proven to be an interesting tool that can be exploited by anyone.
Social engineering consists in the ability to trick someone in believing that he is giving information to someone who has the authority to ask for it. The most common way to do it is through the telephone or via the internet. Let's say that a user receives a call from someone who identifies himself as a system administrator of his company and that he requires some information that could be considered harmless.
It's quite probable that that bit of information is the final piece that the hacker required for finishing his work. Something as innocent as when was the last time that the system asked the user to change his password could be used by him in his advantage.
A quite ingenious method within social engineering was a webpage were users required to enter their mail and password for finding if someone had deleted or blocked them from their Instant Messenger (IM). Unfortunately, many fell under this scheme. Hacking yahoo messenger or any other messenger is quite easy if you find how to exploit the user's needs.
Alternatives used
Besides social engineering, hackers can obtain your password through other means, like worms, viruses or Trojans. Once a hacker is inside your computer, he will look for those files
were your login names and passwords are stored. That's they reason why it isn't considered
safe to store them inside your computer. Even when the provider tells you that it is safe. Remember than there isn't a more secure place for keeping your password than your mind.
Methods Used In The Past !
In the past, one of the common practices used by hacker was using programs that tried different password combinations until it found the correct one. This method was contra rested by email providers by giving a limited number of options or by placing some security measures inside their webpage.
Other method was placing false web pages instead of the original ones. A hacker could make a user think that he is accessing his email at the webpage of his email provider. In reality, he was entering all his information to a webpage created by the hacker. This scheme isn't used any more since users have become a bit more careful and have acquired some concepts on internet security. They have started using secure pages for login which starts
What Are Keyloggers?
Keyloggers are specially devised programs that are installed inside a computer via a Trojan, a virus or a worm. Once inside, the keylogger will auto execute and start recording all the key strokes made by the computer user. Once a determined period of time has gone by, the keylogger will send the keystroke information to the hacker who sent this infectious software.
Then the hacker will start searching key combinations that can lead him to determine the password for determined web pages. This simple and effective method is a favorite among hackers since it can provide them with lots of private information from their victims.
Many computer users have more than one email account, especially if they use the messenger services from multiple providers, like Microsoft's Hotmail, Yahoo's Email or AOL email. It doesn't matter if you have one or many email accounts, every one of them may be a victim of a hacker. Even with the security measures imposed by the companies, Yahoo password hacking or hotmail hacking still exist. And it's very improbable that will disappear.
So, if you want to protect yourself from people who are hacking yahoo accounts or whose whole purpose in life is to do some MSN hacking, then increase the number of special characters in your password and try not to access your email account from a computer that is not yours. And that goes to IM's too. The ability for hacking yahoo messenger or any other IM provider it's a latent danger for all of us.
LOCALLY STORED PASSWORDS |
| Most browsers, including Internet Explorer® and Netscape®, the AOL® client, and Windows® Dial-Up Connections allow you the option to store passwords. These passwords are stored on the local machine and (depending upon where and how it is stored) there is usually a method of recovering these passwords. Storing any password locally is insecure and may allow the password to be recovered by anyone who has access to the local machine. While we are not currently aware of any program to recover locally stored AOL® passwords, we do not recommend that these are secure. Software does exist that can recover most of the other types of locally stored passwords. |
TROJAN |
| A Trojan is a program that is sent to a user that allows an attacker to control functions of the target computer, recover information from the target or to delete or damage files on the target. The name Trojan is given because the program will usually come attached to some other program or file that entices you to run it. There are a wide variety of Trojans any number of which can be programmed to capture passwords as they are typed and to email or transmit them to a third party. To protect yourself against Trojans, you should never execute or download software or files that are not from a trusted source. It is critical that anyone working on internet use a virus protection program (which should catch most Trojans.) Note that since a Trojan requires the password to be typed or stored in order to be recovered, this is not an effective way to recover your own password. It could explain, however, how someone could lose their password to a hacker. Sending someone a Trojan program is certainly illegal and we do not recommend or condone this activity. A Trojan is unlikely to be effective in recovering a particular account password since it requires the target to install it. However, hackers will often bulk mail Trojans to thousands of people in the hope that a small percentage will get caught. Legitimate account holders who may have been caught by a Trojan and can authenticate themselves should contact their service provider to have their account passwords res |
SNIFFING
If two people do not share the same computer, but do share the same network, it may be possible for one to sniff the others' packets as they sign-on. The traffic between your computer and the internet site you are accessing may be able to be recorded and decrypted or "played-back." This is not a simple attack to execute, but is possible if two people are close to one another and share a hub. Again, this is likely to be illegal and we do not condone this activity.This Collection Contains About 250 Wallpapers
There Are Various Wallpapers Like
Skulls,Cool Designs,Cool logos,All The Things An Mobile loving Person Wants
DOWNLOAD
MOBILE/Ipod Wallpapers 2
This Collection Contains About 225 Wallpapers
There Are Various Wallpapers Like
Coolest Cars ,Game ScreenShots,Humourous Wallpapers Etc
DOWNLOAD
Wanna See Some Of Them
MOBILE/IPOD Wallpapers 3
This Collection Contains About 225 Wallpapers
There Are Various Wallpapers Like
Here Are Wallpapers With Attitude
If You have Attitude Problem Download This To Increase ur Problem
DOWNLOAD
Mobile/IPOD Wallpapers 4
This Collection Contains About 275 Wallpapers
There Are Various Wallpapers Like
If U Are looking For Cute Wallpapers This Is The Pack For You
It has Cute Roses,Cute Hearts Etc
DOWNLOAD
Mobile/IPOD Wallpaper 5
This Collection Contains About 275 Wallpapers
There Are Various Wallpapers Like
This pack Contains Logos Of Top Company's And They Are made Comedy In Unique Way
All The Ericson,Nokia,Coco-cola,Adidas,Lacoste , West Coast Customs Logos Are For U
DOWNLOAD
Mobile/IPOD Wallpapers 6
This Collection Contains About 255 Wallpapers
There Are Various Wallpapers Like
All The Scary And Most Funny Wallpapers Here
DOWNLOAD
Note-
Password=www.coolmobileandpc.blogspot.com
Now These Are Wallpapers With Resolution 240x320
Hence They can Be Seen Full Screen in Any Mobile/Ipod
It Supports All Mobiles And Ipod Till Screen Of 3 Inches
Means China mobiles With Huge Screens Are Too Supported
IF U Need Any Type Of Wallpapers Then Contact Me
Breaking the Restrictions of the Administrator
Author: @k$h@y // Category:A Loophole u never knew about
This works on WIn 2000 & WIN XP.
Dis can be used to gain access to the website you want to
for free, and how you can gain access to 'control panel', and the various
other tools of Widows that may have been blocked from your grasp like 'regedit' by the administrator. IT can be used in schools & colleges..
When u are at the log on screen, type in your username and
password. NOW When you hit enter, and it comes up with
the next screen, the rectangle one, immediatly pull out the network
cable i.e. the cable wire.
Now u can log on without any restrictions because when the cable is pulled off then it does not download any settings from the server. Now you have access to control panel, & all the other features which had been blocked BUT there will be no
network access. But that's cool because now we can access 'Internet options',
click in the 'connections' tab click the LAN settings, click the proxy
settings, and in the little white box at the bottom we can specify websites
that bypass the proxy server (eg www.yahoo.com) Now once you have changed
the settings to what you wish, apply them and restart the computer. Now get someone else to log onto it because if you log in it will load the cached settings from your previous log in, then after the other person logs in, everyone that logs in after them included themselves will have the
internet settings you specified.
Its only an 'Unplugging technique' to gain access to a comp. locked by the administrator.
Now you can gain access to msconfig, regedit, command etc disable the virus scanner, or to install a trojan or a virus according to u're will..
XP HOME ADVANCED FILE PERMISSIONS.!!
Access *Advance file Permissions* on NTFS file systems for XP Home simply by booting into *Safe Mode*, rt-clicking any file or folder, and navigating to the *Security tab*. This gives the user the ability to allow or deny read, write, execute, read & write, display contents, full-control, iheritance, and take ownership permissions, with many more options available to apply to different users and groups stored on the computer. Well, you don't have to do this in *Safe Mode* (XP Home). Although it is a little less intuitive, you can simply go to your command prompt - Start>All Programs>Accessories>Command Prompt. Now type "cacls" in the window (without the quotes). This gives you the ability to add, remove or modify file permissions on files and folders through the command prompt. Type "cacls /?" for help on different options and variables. You do not need to be in safe mode to use this so it makes it a little quicker than using the safe mode security tab GUI. Remember - this only applies to NTFS. Here also is a very useful link to find a lot of extras and tweaks straight from the horse's mouth - the Microsoft Resource Center. You will find a lot of very useful web-based extra's here, most of them left unknowing to the general public - such as, "Online Crash Analysis" - a site that looks like Windows Update but you can upload your crash "dump logs" (when you get those system or application crash error reports). Microsoft will then analyze the log file and tell you some more info about WHY the system crashed (ie. faulty hardware/software/conflicts, etc).
Smart NTFS Recovery is a data recovery tool for Windows operating system that supports the NTFS file system.Smart NTFS Recovery easily recovers data from hard disks and any type of storage media - USB drives, flash drives, PC card, memory stick, multimedia card, secure digital card with NTFS file system.
Smart NTFS Recovery applies a simple yet powerful algorithm, which makes it possible to restore your lost data quickly and effectively.Smart NTFS Recovery can recover any deleted files, including MS Office
files, photos, mp3 and zip files.
Smart NTFS Recovery is able to restore all sorts of files, including electronic documents and pictures. It restores files from NTFS hard drives, has really simple interface and is compatible with Windows operations systems. Our aim is to prevent information loss, and prevent you from wasting your time and money.
For different reasons, important documents and user files are sometimes lost. Without a recovery tool for documents and files, this may become a huge problem (one that leads to considerable inconveniences, and requires expensive solutions).
The software enables to remove the data concerning deleted files. Thus nobody will be able to recover the data deleted by you and use it in own interest
Author: @k$h@y // Category: Hacking Tools, New PC GAMES Full Version, New PC Softwares, Windows Tricks

Locate Laptop 1.0 Anti-Theft and Tracking system. A recent survey stated that on an average 60 laptops are stolen or lost every week! What you lose is not only the laptop, but also valuable, sensitive and creative information in it. Do you have a plan to counter this yet? Locate Laptop is a system that locates reportedly stolen laptop, from the world wide web. And what more, it silently transfers your critical information on our secure data server. Laptop Locator also encrypts your sensitive information, without the knowledge of the offender!
Features:
* Provides current location along with IP address and service provider.
* Customise reporting on Laptop Location as per your choice.
* Secure web page for every user to monitor the laptop/ persons location.
* Remotely launch the data encryption once theft is reported.
* Automatic/ silent data encryption if Laptop is not connected to internet for a specified period.
* Works in stealth mode.
Advantages:
* Fastest tracking of Laptop once theft is reported.
* Tracks the laptops/ Employee locations on regular basis.
* Protects Sensitive data/ information being used by competitors due to Laptop theft.
* Online location statistics is available any time from any where through www.locatelaptop.com.
* Reporting via email on regular intervals as per your choice.
Homepage: www.locatelaptop.com

- Now make Ur Windows Xp Geniune Using These Softwares
Windows Genuine Advantage Validation 1.7.18.1
or
Windows Genuine Advantage Validation v1.9.9.1 CRACKED
OR
Speed Up XP Booting.
Author: @k$h@y // Category:Locate the following key in the registry:
HKEY_LOCAL_MACHINE\SYSTEM\Current ControlSet\Control\Ses sionManager\MemoryManagement\Prefetch Parameters
Make sure you backup the keys by exporting them to a .reg file.
On the EnablePrefetcher value, change the setting from 3 to 5 (decimal).
Close the registry editor.
Restart your computer.
Windows Password Loophole
Author: @k$h@y // Category:b. and click on local users and groups.
c. once you've gotten here you need to open up the 'users' folder.
at this point i am walking along with you and notice that there are several
major security holes dealing specifically with the password:
1. double clicking on the any user name allows you a list that looks
something like this:
"user name"
full name: -----------------------
|__________________|
description: -----------------------
|__________________|
--
|_| user must change password at next logon
--
|_| user cannot change password
--
|/| password never expires
--
|_| account is disabled
--
|_| account is locked out
"ok" "cancel" "apply"
ok if you can get past my cheesy drawing, i must ask, did you notice that
the "password never expires" box is checked? if you did, then you may have
realized that this means that you can also uncheck it!
2. if ure paying attention, you'll see that the 'user must change password
at next logon' box is unchecked. if you put a check in this box of course,
when you shut down the system will prompt for a new password!
3. going back to step c.,
right click on any account and notice the dialoge that appears:
set password...
all tasks
delete
rename
properties
help
i think you can handle it from here
ps. i wonder if you can access this data if this stuff is locked to the user
by the admin by going in through the command prompt. i doubt it but if anyone
finds a way let me know.
Find who is Invisible on Yahoo messenger
Author: @k$h@y // Category:There is this small trick that you can use to find out what the truth is.
Firstly open your yahoo messenger main window and double click on the name of the person whom you want to check.The chat window will open obviously.
Click IMVironment button, select See all IMVironments, select Yahoo! Tools or Interactive Fun, and click on Doodle.
After loading the Doodle imvironment there can be two possibilities
1.If the user is offline Doodle are will show this "waiting for your friend to load Doodle" continuously .See in the picture below:
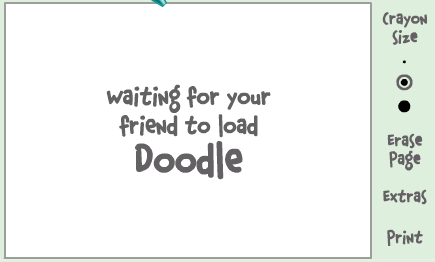 2. If the user is online (but in invisible mode), after few seconds (it can take up to one minute, depending on your connection speed), you should get a blank page like in the picture below.So you know that the user is online.
2. If the user is online (but in invisible mode), after few seconds (it can take up to one minute, depending on your connection speed), you should get a blank page like in the picture below.So you know that the user is online.
Alternate Method:
Chose a person you want to check .Double click to open the chat window.Now simply invite the person for a voice conference.This is done by clicking on the "conference' button on the top of the chat window.
If the talk button appears and turns green then that person is online.But if you receive the message 'Voice chat could not be started ' then the person is offline.
Note:Some people use softwares like buddy spy to check who is invisible.I DONT RECOMMEND you to use such third party softwares as they can expose your Pc to hackers by sending your personal information and can even steal information from your Pc.So avoid such softwares and instead use the simple tricks given above.
If you have any queries or would like to make some useful contribution to this topic feel free to drop a line in the comments section.
Nokia N73 Stuff
Author: @k$h@y // Category: China Mobile Mania, Cool Mobile Games, Mobile hacks, Nokia Mobile CodesCool jar mobile Games
Author: @k$h@y // Category: China Mobile Mania, Cool Mobile Games, Hacking Tools, Make Your S/W Cracks
I am going to share all these Games with you. There is no problem with which Mobile you have since these games will run on all the Mobile Phones which has Java Support since all these games are in jar format. User having small resolution screen of 178×208 should not get Depressed since these games will be working perfectly on their Mobiles also.

orkut scrapbook flooder trick...
Author: @k$h@y // Category:Getting original xp key from pirated XP CD!!
2. Right click it and select open.
3. Open the folder named I386.
4. In this folder there is a note pad file UNATTEND.txt
5. Open this file and browse till the last line.
6. You'll find there a original xp key.
7. Use this key while installing xp and there are 98% chance that your copy of XP will come out of Windows validation as a geniune copy.
This will help u make windows xp geniune with out patch or some files..

orkut scrapbook flooder trick...
javascript:text=prompt("Enter text to be flooded");ctr=0;function scrapflood(){ctr=ctr+1;parent.orkutFrame"+"
"+ctr;parent.orkutFrame._
just copy and paste the above script in ur scrapbuk....in the adress bar were u type google . com............
window will apear..add ur text there ...wait for 5 secons ....there u go..
remember dont use script more than 1 time per day or ur account will freeze...
put catapacha wen appear.. if u dont even ur account may freeze..
hope u all lik it.

It Is a radio communications technology that will create a "bit pipe" for providing mobile access to internet-based services. It will enhance and extend mobility in many areas of our lives.In the near future, mobility won't be an add-on: it will become a fundamental aspect of many services. We'll expect high-speed access to the internet, entertainment, information and electronic commerce (e-commerce) services wherever we are - not just at our desktop computers, home PCs or television sets.
3G services will add an invaluable mobile dimension to services that are already becoming an integral part of modern business life: Internet and Intranet access, video-conferencing, and interactive application sharing
Combines a mobile phone, laptop PC and TVFeatures includes:- Phone calls/fax- Global roaming- Send/receive large email messages- High-speed WebNavigation/mapsVideoconferencing- TV streaming- Electronic agenda meeting reminder.Speed: 500kb/sec-5mb/sec (Download Speed)Time to download a 3min MP3 song: 10sec-1min
Capability to support circuit and packet data at high bit rates: - 144 kilobits/second or higher in high mobility (vehicular) traffic - 384 kilobits/second for pedestrian traffic - 5 Megabits/second or higher for indoor traffic
Interoperability and roaming
Common billing/user profiles:- Sharing of usage/rate information between service providers- Standardized call detail recording- Standardized user profiles Capability to determine geographic position of mobiles and report it to both the network and the mobile terminal
Support of multimedia services/capabilities:- Fixed and variable rate bit traffic Bandwidth on demand- Asymmetric data rates in the forward and reverse links- Multimedia mail store and forward- Broadband access up to 5 Megabites/second
Key features of 3G systems are a high degree of commonality of design worldwide, compatibility of services, use of small pocket terminals with worldwide roaming capability, Internet and other multimedia applications, and a wide range of services and terminals. According to the International Telecommunication Union (ITU) International Mobile Telecommunications 2000 initiative ("IMT-2000") third generation mobile ("3G") system services are scheduled to be initiated around the year 2000, subject to market considerations. We're likely to see 3G services enter our day -to-day lives in all sorts of new ways: for example, in shopping, especially Internet "mail order" (e-commerce), banking, or playing interactive computer games over the Net.We'll think nothing of sitting on a train and using a mobile palmtop with Internet browser to log into our bank accounts. While on-line we'll be able to check our accounts, pay a few bills and click on a screen icon to immediately set up a video-conference to discuss our account with a bank clerk.
Increasingly, machine-to-machine communications will also be enabled and enhanced with future mobile network technology. Domestic appliances will have built-in radio modems to provide remote control and diagnostics. Our refrigerators will have built-in sensors that detect which items need restocking and automatically send a reminder message to our Personal Digital Assistants (PDAs). We could even get the refrigerator to send an order direct to our local store. Likewise, vending machines will be able to tell the warehouse when they need restocking.
IN INDIA 3G Service Has Started
Till Now BSNL And Vodaphone Have Started This Service
I Doubt Vodaphone Has Started It Or Not
But Bsnl Has Started Their 3G Service
Some Rates For Bsnl 3G Service(3G Sim)
0.75 Rs. Per Mb Downloadeded Or Uploaded
All Call Rates Are Same As To Bsnl GSM Prepaid
You Need An Good HandSet(E Series,N Series,Iphone) To Use 3G Efficiently
It is Of No Use That You Insert An 3G Enabled Sim In Ur 6600
BSNL Gives Follwing Features On Their 3G Network
Direct TV On Mobile
Download Speed Upto 1 Mb/Sec(In UK Vodaphone Gives 3.6 Mb/sec)
Direct Access To All Sites On Net (Including All Ftp As Well As HTTP )
Source: Google And Some Friends
For More Keep Visiting
www.coolmobileandpc.co.cc
R C Generator Help
Author: @k$h@y // Category:Here Is The Help File
Some Direct Recharge Codes And More
Download It Here
I Am Sure You Will Be Able to Use The Recharge Code Generator After Reading This File
Recharge Code Generator Updated Version
Author: @k$h@y // Category: Internet Explorer 8
Internet Explorer 8See how we help you search smarter, work faster, and browse more safely—all within a familiar environment. Install Windows Internet Explorer 8, MSN Toolbar, and Microsoft Silverlight in one click.
Microsoft've made major improvements, to put the Web at your service and make Internet Explorer 8 the best browser for everyday use.
- Complete your everyday browsing activities like mapping directions, translating words, e-mailing friends, and more in just a few clicks.
- Browse the Web on a shared computer without leaving a trace, or shop for that special gift without anyone finding out, using InPrivate Browsing.
- Keep up with changes to the sites you care about most with the new Web Slices feature. Add a Web Slice and you won't have to go back to the same Web site again and again for updates on news, stock quotes, online auctions, weather, or even sports scores.
- Search smarter with detailed suggestions from your favorite search providers and browsing history. See visual previews and get suggested content topics while you type in the enhanced Instant Search Box.
- New security features help to protect you against deceptive and malicious Web sites which can compromise your data, privacy and identity.
Features: What's new in Internet Explorer 8
View any site with ease
 Now you can quickly display websites that were designed for older browsers. If you’re looking at a page and the text or images aren’t lined up right, just use the new Compatibility View button next to the Refresh button on the Address Bar.
Now you can quickly display websites that were designed for older browsers. If you’re looking at a page and the text or images aren’t lined up right, just use the new Compatibility View button next to the Refresh button on the Address Bar.Get things done faster with Accelerators
 You're just a few mouse clicks away from driving directions, word translation, sharing your web discoveries with friends and more. Accelerators help you do the things you do all the time without having to open up a new window. So you can speed through everyday browsing tasks, like getting a map to a business address or forwarding a link to a friend.
You're just a few mouse clicks away from driving directions, word translation, sharing your web discoveries with friends and more. Accelerators help you do the things you do all the time without having to open up a new window. So you can speed through everyday browsing tasks, like getting a map to a business address or forwarding a link to a friend.Stay safer online
-------------------------------------------------------------------------------------------------
Operating System - Windows Vista / Windows XP
File Name - Internet Explorer
Version - 8.0
Date Published - 19/03/2009
Language - English
Download Size - 16.1 MB
-------------------------------------------------------------------------------------------------
Download Internet Explorer 8.0 for Windows XP -- Click Here
Download Internet Explorer 8.0 for Windows Vista -- Click Here
-------------------------------------------------------------------------------------------------
 Netscape Navigator 9.0.0.5
Netscape Navigator 9.0.0.5In addition to high-speed browsing and instant-messaging capabilities, Netscape features one-click searching from the address bar; Quick Launch, which reduces the browser start-up time; Click-to-Search, which allows users to select a word within a Web page and search; improved instant messaging, including support for buddy icons, file transfers, and buddy alerts; and tabbed browsing, which allows users to view multiple Web pages in a single browser window.
Version 9.0.0.5 includes unspecified updates.
-------------------------------------------------------------------------------------------------
Operating System - Windows XP, Windows Vista, Windows Me, Widnows 2000, Windows 98
-------------------------------------------------------------------------------------------------
Download Netscape Navigator -- Click Here
-------------------------------------------------------------------------------------------------
 Google Chrome
Google ChromeGoogle Chrome is a browser that combines a minimal design with sophisticated technology to make the Web faster, safer, and easier. Use one box for everything--type in the address bar and get suggestions for both search and Web pages. Thumbnails of your top sites let you access your favorite pages instantly with lightning speed from any new tab. Desktop shortcuts allow you to launch your favorite Web apps straight from your desktop.
Version 0.2.149.30 is a security and bug-fixing update.
-------------------------------------------------------------------------------------------------
Operating System - Windows XP, Windows Vista
-------------------------------------------------------------------------------------------------
Download Google Chrome -- Click Here








Previous Winner